Building a Better Tower – Cybersecurity
February 18, 2021

Tower has invested in significant cybersecurity initiatives to “Build a Better Tower” for our clients. I provided a brief overview of those initiatives in a recent article and this week I highlight Tower’s investment in protecting Tower and our clients’ data.
Tower’s Cybersecurity Defenses
Long before COVID-19 came along, bringing a tsunami of cyberattacks, Tower had already proactively strengthened our internal IT defenses.
During the fall of 2019 we partnered with Vigilant Technology Solutions to use a service that combines passive monitoring technology with certified information security analysts. Through a customized deployment of Vigilant’s NDR (Network Detection and Response) and EDR (Endpoint Detection and Response) technology, Vigilant’s analysis engines and human threat hunting has reduced the time to detect and contain threats by 99.97% over the industry average. Without this kind of 24/7/365 monitoring and action, bad actors can enter a system undetected and stay there for months learning how to circumvent security measures and destroying backup data resources.
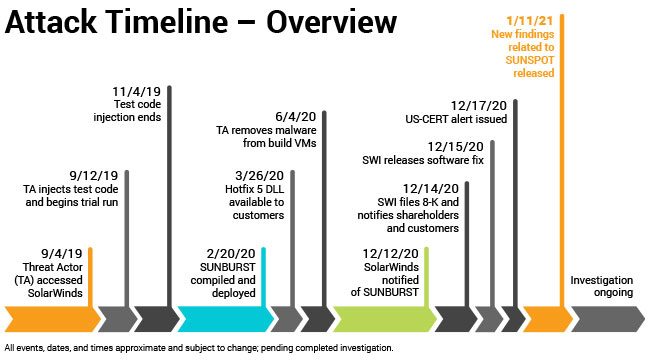
The graph below shows the timeline of the recent attack on SolarWinds that ultimately compromised 18,000 through deployed software. SolarWinds CEO disclosed an updated attack timeline, indicating that hackers had first accessed SolarWinds on September 4, 2019. Source: SolarWinds blog, January 11, 2021.
But it is not sufficient to protect our own technology. We also educated our clients and others in the industry so they could understand and prevent cyber threats. Vigilant’s CEO Chris Nyhuis joined our VP of Information Technology Jesse Shade and another expert, Rob Kolb of Premier Mindset, for an eye-opening webinar in February. It’s available on demand. Jesse also wrote two WorkCompWire articles with excellent advice that you can read here and here.
Third-Party Risk Assessments
In addition to ensuring the protection of its internal data, Tower also implemented a Vendor Risk Assessment Process for all third parties that had access to Tower data or networks or housed servers that stored our data. Our philosophy is that we are only as strong as our weakest link. The result of this assessment is a vendor management process that continuously measures and monitors our partners to ensure that as per the AICPA Trust Criteria, we consistently honor the commitments made to our clients.
These are just a few of the ways that Tower is continually and proactively enhancing our infrastructure, processes and offerings to deliver measurably better services to you.
Rita Wilson,
Chief Executive Officer

